Disney前Fox团队发布的ST2110-40解剖器
SMPTE ST 2110-40 dissector
Dissector for SMPTE ST 2110-40 Ancillary Data
Lua Dissector for ST 2110-40 in Wireshark
Project Lead: Thomas Edwards (thomas.edwards@disney.com)
to use in Wireshark:
- Ensure your Wireshark works with Lua plugins – "About Wireshark" should say it is compiled with Lua
- Install this dissector in the proper plugin directory – see "About Wireshark/Folders" to see Personal and Global plugin directories. After putting this dissector in the proper folder, "About Wireshark/Plugins" should list "ST-2110_40.lua"
- In Wireshark Preferences, under "Protocols", set st_2110_40 as dynamic payload type being used
- Capture packets of ST 2110_40
- "Decode As" those UDP packets as RTP
- You will now see the ST 2110_40 Data dissection of the RTP payload
- You can extract the Closed Captionning Data with the script parse_CC.sh. The utility tshark has to be installed. The script extracts with tshark the CC Data from a pcap file and concatenates them into an output file:
./parse_CC.sh --in=<PCAP_FILE> --out=<CC_DATA_EXTRACTED_FILE>or to output in stdout:
./parse_CC.sh --in=<PCAP_FILE> -v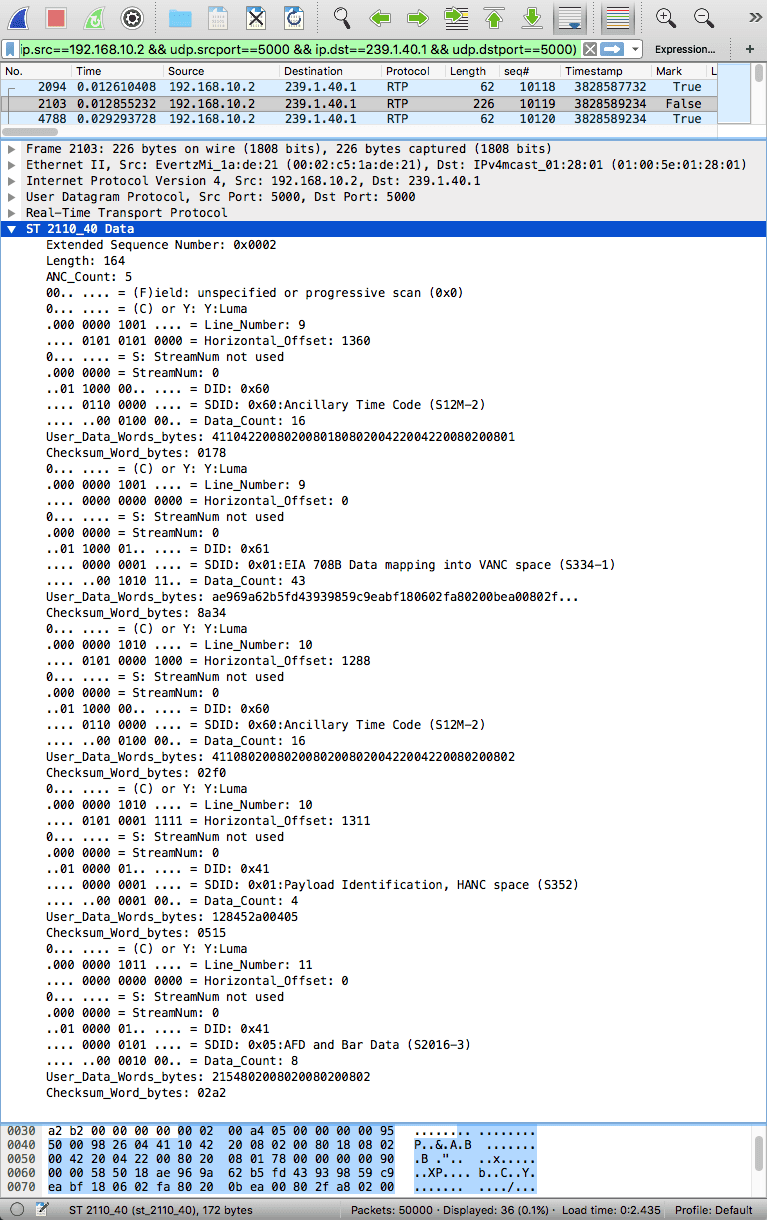
This program is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation; either version 2 of the License, or (at your option) any later version.
https://github.com/NEOAdvancedTechnology/smpte2110-40-dissector